This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

Bypass traverse checking
Applies To: Windows Vista, Windows Server 2008, Windows 7, Windows 8.1, Windows Server 2008 R2, Windows Server 2012 R2, Windows Server 2012, Windows 8
This security policy reference topic for the IT professional describes the best practices, location, values, policy management, and security considerations for this policy setting.
This policy setting determines which users (or a process that acts on behalf of the user’s account) have permission to navigate an object path in the NTFS file system or in the registry without being checked for the Traverse Folder special access permission. This user right does not allow the user to list the contents of a folder. It only allows the user to traverse folders to access permitted files or subfolders.
This policy setting is supported on versions of Windows that are designated in the Applies To list at the beginning of this topic.
Constant: SeChangeNotifyPrivilege
Possible values
User-defined list of accounts
Not Defined
Best practices
Use access–based enumeration when you want to prevent users from seeing any folder or file to which they do not have access.
Use the default settings of this policy in most cases. If you change the settings, verify your intent through testing.
GPO_name \Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment
Default values
The following table lists the actual and effective default policy values for the most recent supported versions of Windows. Default values are also listed on the policy’s property page.
Operating system version differences
There are no differences in the way this policy setting works between the supported versions of Windows that are designated in the Applies To list at the beginning of this topic.
Policy management
Permissions to files and folders are controlled though the appropriate configuration of file system access control lists (ACLs).The ability to traverse the folder does not provide any Read or Write permissions to the user.
A restart of the computer is not required for this policy setting to be effective.
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on.
Group Policy
Settings are applied in the following order through a Group Policy Object (GPO), which will overwrite settings on the local computer at the next Group Policy update:
Local policy settings
Site policy settings
Domain policy settings
OU policy settings
When a local setting is greyed out, it indicates that a GPO currently controls that setting.
Security considerations
This section describes how an attacker might exploit a feature or its configuration, how to implement the countermeasure, and the possible negative consequences of countermeasure implementation.
Vulnerability
The default configuration for the Bypass traverse checking setting is to allow all users to bypass traverse checking. Permissions to files and folders are controlled though the appropriate configuration of file system access control lists (ACLs) because the ability to traverse the folder does not provide any Read or Write permissions to the user. The only scenario in which the default configuration could lead to a mishap would be if the administrator who configures permissions does not understand how this policy setting works. For example, the administrator might expect that users who are unable to access a folder are unable to access the contents of any child folders. Such a situation is unlikely, and, therefore, this vulnerability presents little risk.
Countermeasure
Organizations that are extremely concerned about security may want to remove the Everyone group, and perhaps the Users group, from the list of groups that have the Bypass traverse checking user right. Taking explicit control over traversal assignments can be an effective way to limit access to sensitive information. Access–based enumeration can also be used. If you use access–based enumeration, users cannot see any folder or file to which they do not have access. For more information about this feature, see Access-based Enumeration .
Potential impact
The Windows operating systems and many applications were designed with the expectation that anyone who can legitimately access the computer will have this user right. Therefore, we recommend that you thoroughly test any changes to assignments of the Bypass traverse checking user right before you make such changes to production systems. In particular, IIS requires this user right to be assigned to the Network Service, Local Service, IIS_WPG, IUSR_ <ComputerName> , and IWAM_ <ComputerName> accounts. (It must also be assigned to the ASPNET account through its membership in the Users group.) We recommend that you leave this policy setting at its default configuration.
User Rights Assignment
Additional resources
WinSecWiki > Security Settings > Local Policies > User Rights > User Rights In-Depth > Bypass traverse checking
Bypass traverse checking
AKA: SeChangeNotifyPrivilege, Bypass traverse checking
Default assignment on workstations and member servers: Administrators, Backup Operators, Power Users, Users, Everyone
Default assignment on domain controllers: Administrators, Authenticated Users
Leave this one alone. Technically this right ensures you can access a file several levels down in the folder hierarchy even if you lack permissions to the parent folders – provided of course you have permissions to the object itself and know its fully qualified pathname. Without this right Windows would require you to have permissions to all parent folders in addition to the file being accessed. I say leave it alone because revoking this right can cause a number of problems such as with IIS and even blue screens of death (BSODs).
This right is also reportedly required for applications that register with Windows to be notified of changes to the file system – as in how Windows Explorer efficiently and immediately updates windows Whenever files are added/removed by some other program or user on the network.
By default this right is not audited even if you enable Audit privilege use . See Full Privilege Auditing.
Back to top

Set and Check User Rights Assignment via PowerShell
You can add, remove, and check user rights assignment (remotely / locally) with the following powershell scripts..
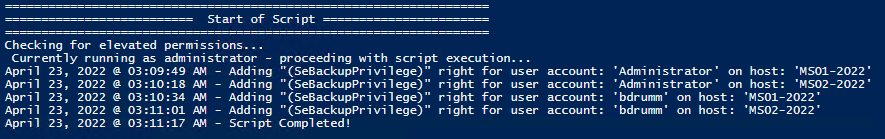
Posted by : blakedrumm on Jan 5, 2022

Local Computer
Remote computer, output types.
This post was last updated on November 5th, 2024
I stumbled across this gem ( weloytty/Grant-LogonAsService.ps1 ) that allows you to grant Logon as a Service Right for a User. I modified the script you can now run the Powershell script against multiple machines, users, and user rights.
Set User Rights
How to get it.
All of the User Rights that can be set:
Note You may edit line 564 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the PowerShell ISE.
Here are a few examples:
Add Users Single Users Example 1 Add User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -AddRight -UserRight SeInteractiveLogonRight Example 2 Add User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Add User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Add User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -AddRight -Username S-1-5-11 -UserRight SeBatchLogonRight Add Multiple Users / Rights / Computers Example 5 Add User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -AddRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName " $ env : COMPUTERNAME " , "SQL.contoso.com" -UserName "CONTOSO\User1" , "CONTOSO\User2"
Remove Users Single Users Example 1 Remove User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -RemoveRight -UserRight SeInteractiveLogonRight Example 2 Remove User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Remove User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Remove User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -RemoveRight -Username S-1-5-11 -UserRight SeBatchLogonRight Remove Multiple Users / Rights / Computers Example 5 Remove User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -RemoveRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName " $ env : COMPUTERNAME " , "SQL.contoso.com" -UserName "CONTOSO\User1" , "CONTOSO\User2"
Check User Rights
In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your PowerShell ISE and press play.
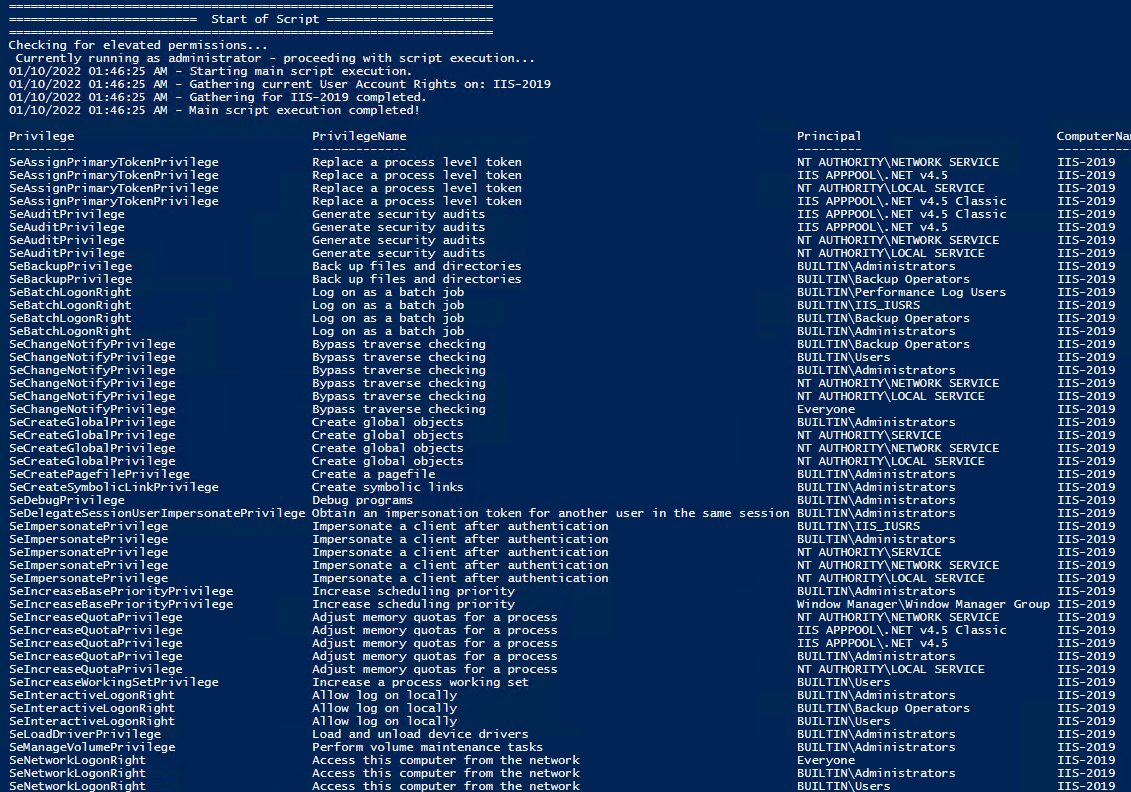
Note You may edit line 493 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the PowerShell ISE.
Get Local User Account Rights and output to text in console:
Get Remote SQL Server User Account Rights:
Get Local Machine and SQL Server User Account Rights:
Output Local User Rights on Local Machine as CSV in ‘C:\Temp’:
Output to Text in ‘C:\Temp’:
PassThru object to allow manipulation / filtering:
I like to collaborate and work on projects. My skills with Powershell allow me to quickly develop automated solutions to suit my customers, and my own needs.
Email : [email protected]
Website : https://blakedrumm.com
My name is Blake Drumm, I am working on the Azure Monitoring Enterprise Team with Microsoft. Currently working to update public documentation for System Center products and write troubleshooting guides to assist with fixing issues that may arise while using the products. I like to blog on Operations Manager and Azure Automation products, keep checking back for new posts. My goal is to post atleast once a month if possible.
- operationsManager
- troubleshooting
- certificates
- containerapps

- NIST 800-53
- Common Controls Hub
Unauthorized accounts must not have the Bypass traverse checking user right.

Windows security encyclopedia
#microsoft #windows #security
Search form
Bypass traverse checking.
This user right determines which users can traverse directory trees even though the user may not have permissions on the traversed directory. This privilege does not allow the user to list the contents of a directory, only to traverse directories.
This user right is defined in the Default Domain Controller Group Policy object (GPO) and in the local security policy of workstations and servers.
Policy path:
Comments: , default: , supported on: , registry settings: , reboot required: , related content.
Tim’s Tech Blurbs
Tim’s tech ramblings about Intune, Modern Management, Powershell and every thing else.
How to move Windows 10 User Rights Assignment to Endpoint Manager / Intune
Should you change the default user rights assignments in Windows 10? That’s the question. If you ask my college the AD expert, he will tell you to run away and don’t even think about changing the defaults. (He will back it up with some pretty funny stories as well about who someone did it and locked out a company and maybe even a ship)
If you ask the Security team, the answer is a yes. We should set them.
Let taks a look. We will start at my favourite site. The Windows 2004 security baseline. MS recommend quite a few setting to be applied. When we add another baseline from the Security team we end up with the table below.
First things first. Let’s check the CSP and see what we need to do. To note, you can user the nice name for the account. (i.e Administrators). But we have ever lanuguage under the sun. So we need a better way to define the accounts. Lets check the Well know SID Structures for what we need.
Lets start with the local administrator. When you check for the SID, be sure to look for the BUILTIN groups and not the domain Groups. Looking at the table the SID is S-1-5-32-544.
Now we check the local account and we get S-1-5-113.
So Lets set up a polcy. Lets open Endpoint Mananger.
Goto Devices -> Configuration Profiles. Select Add new.
Select “Windows 10 and Later” and Custom in the profile
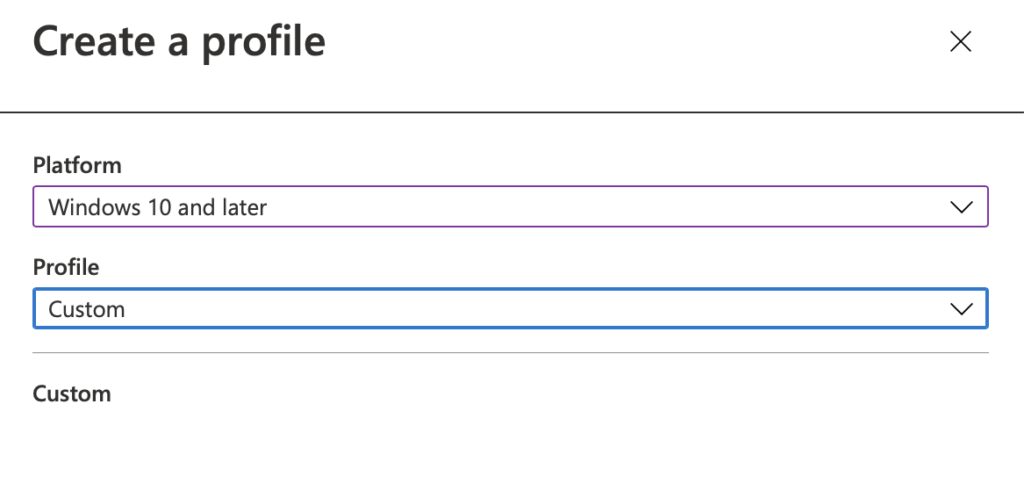
Let’s enter in a Logical name. “Windows 10 User Rights Assignment” and select Save.
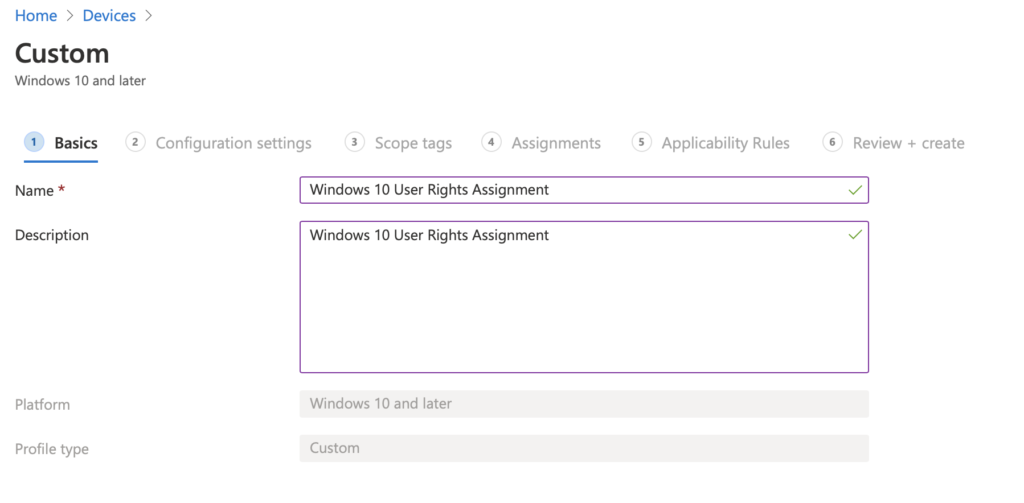
Lets Start with “Load and unload device drivers.” Select Add on the next Page. Enter in the name for the setting. I am preceding the name with URA (for User Rights Assignment). In the OMA-URI after in ./Device/Vendor/MSFT/Policy/Config/UserRights/LoadUnloadDeviceDrivers The Data Type should be string. Andter in the desired SID for the setting. In this case it will be *S-1-5-32-544. (Add the * in before to distinguish its a SID) Pres Save.
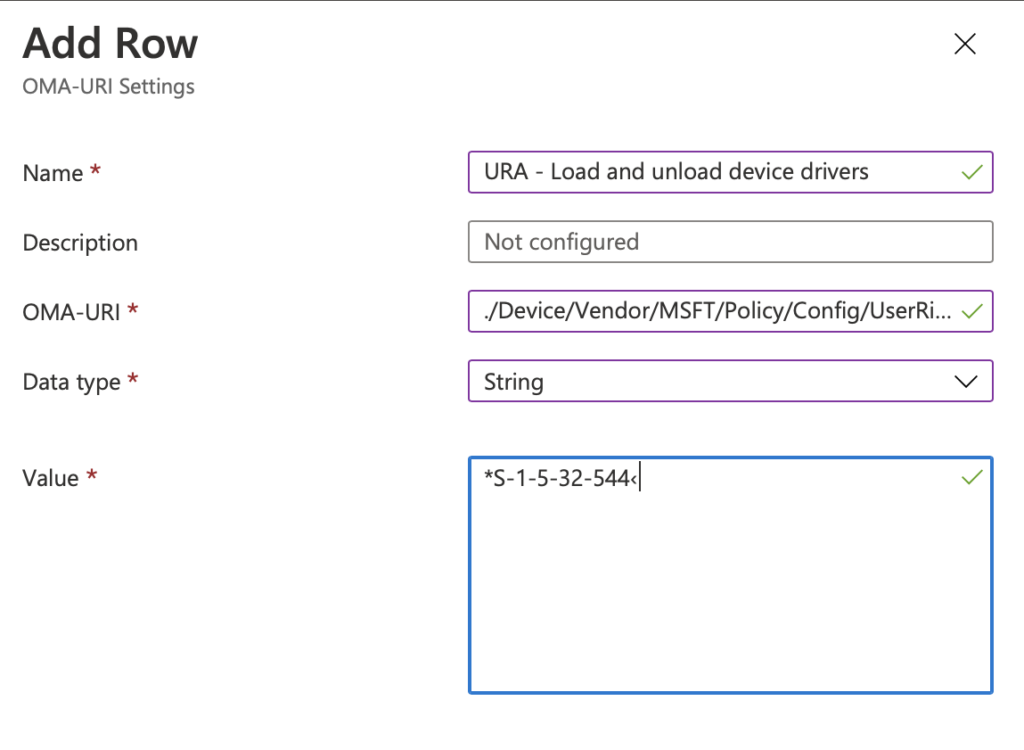
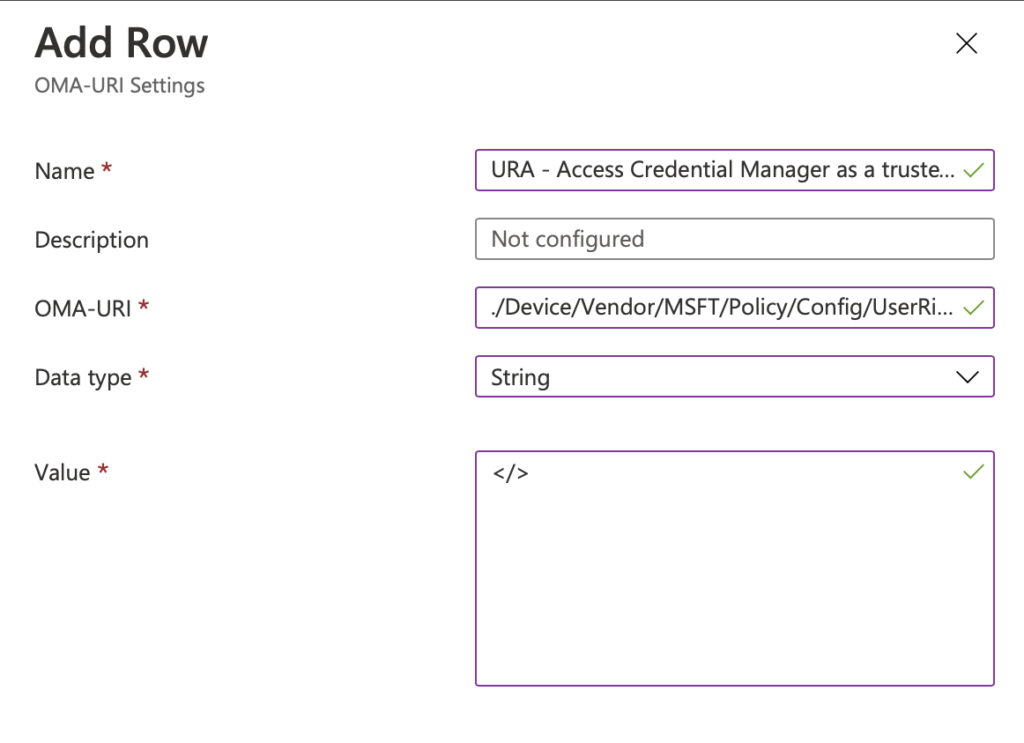
Done. What’s next. Lets go “Access Credential Manager as a trusted caller”. According the baseline no one should have access to this. But how do we define it so no one can access it. Well don’t press save with a blank field. It will fail (I learn the hard way)
Add a new one and add in the name URA – Access Credential Manager as a trusted caller. Then for the OMA-URI enter in ./Device/Vendor/MSFT/Policy/Config/UserRights/AccessCredentialManagerAsTrustedCaller. Select String again. In the data field I have set the value as </>. If you leave it black you get an error when saving it. Its really annoying if you have added 20 on and then relies they have all failed.
Repeat until you have added them all in. Select Next, and then assign them to your test group. Sync your device, and reboot.
You should also do the testing on a test machine. Just in case you lock your self out.
How can you check the User rings assignments have worked? Lets ask Mark. He usually know these things.
Lets download AccessChk from here. https://docs.microsoft.com/en-gb/sysinternals/downloads/accesschk . It allows you to check various permissions fo r files register etc. We will use it with the -a to give us the Windows account right. Lets check SeSystemtimePrivilege or Change the System time. According to the baseline, only Admin and Local services should have this right. Lets run accesschk.exe -a SeSystemtimePrivilege
Great the values are as we expect. What about the checking all the permissions. Let’s run accesschk.exe -a * to show all the permissions.
Now all the rights look good. So lets plan to roll it out and hope we don’t become a funny storey for my college
Published by Tim Wood
Privacy overview.
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Give access to a subdirectory without giving access to parent directories
I have a scenario involving a Windows file server where the "owner" wants to dole out permissions to a group of users of the following sort:
- \\server\dir1\dir2\dir3 : read, write and execute
- \\server\dir1\dir2 : no permissions
- \\server\dir1 : no permissions
- \\server : read and execute
To my understanding ( Update : This entire paragraph is wrong!), it is not possible to do this because Read & Execute permission must be granted to all the parent directories in a directory chain in order for the operating system to be able to "see" the child directories and get to them. Without this permission, you can't even obtain the security context token when trying to access the nested directory, even if you have full access to the subdirectory.
We are looking for ways to get around this, without moving the data from \\server\dir1\dir2\dir3 to \\server\dir4 .
One workaround I thought of, but which I am not sure if it will work, is creating some sort of link or junction \\server\dir4 which is a reference to \\server\dir1\dir2\dir3 . I am not sure which of the available options (if any) would work for this purpose if the user does not have Read & Execute permission on \\server\dir1\dir2 or \\server\dir1 , but as far as I know, the options are these:
- NTFS Symbolic Link,
So the questions:
- Are any of these methods suitable to accomplish my goal?
- Are there any other methods of linking or indirectly referencing a directory, which I haven't listed above, which might be suitable?
- Are there any direct solutions that don't involve granting Read & Execute to \\server\dir1 or \\server\dir2 but still allowing access to \\server\dir1\dir2\dir3 ?
- windows-server-2003
- symbolic-link
- This is possible. The user would see the directory but if not given read permission, can not see the contents of the directory at all, easy enough to setup. – Ramhound Commented Dec 17, 2012 at 17:15
- That was my question too. Thank you for raising the discussion. And for updating your question to reflect immediately that your assumption was wrong. – tyron Commented Mar 21, 2014 at 12:51
4 Answers 4
You are mistaken in your original assumption, which renders the rest of your question moot.
The minimum permission that a user would need on dir1 and dir2 is Traverse Directory . This will most likely be problematic to your users, though - so I would recommend Traverse Directory and List Folders . They will be able to navigate through the top two directories and get to dir3 where they have more permissions, but will not even see what files exist in the top two directories.
Permissions like Read & Execute and Modify are just collections of individual permissions. They're the first thing you see, because they're the most commonly used. If you need to get very granular (like this situation), click the Advanced button and dig into the options listed there.
- Excellent information (2)! But there is something I didn't catch up: "This will most likely be problematic to your users, though". Why would it be problematic? The naming is pretty straightforward in the sense that "Traverse" seems the only needed permission. What kind of problems should users expect? – tyron Commented Mar 21, 2014 at 12:50
Amazingly, if the individual has the full path to a subfolder on which they have at least R permissions, they require NO permissions on any of the parent folders, not even traverse. They can simply access it using the UNC. (They must, of course, have read permissions on the share; just not on any folders above the level they want to access).
I didn't believe this when I was told, but testing proves it out.
This is counter to what I thought I knew of permissions in the Windows world, and I suspect will be a surprise to many.
\server\folder1\folder2\folder3
If there are no permissions at all for Bilbo on folder1 and on folder2, but Bilbo has modify (for example) on folder3, \server\folder1\folder2\folder3 will take him right there, no problem.
- This works when folder1 has SHARE permissions and NTFS permissions are set on folder3 So this \\server\c$\folder1\folder2\folder3 wont work. – user2304170 Commented Jun 8, 2017 at 9:41
- 2 To add to this answer, this implicit "ability" to traverse parent folders to a subfolder, however deep, to which you have access is granted by the user right called "Bypass Traverse Checking" granted in Group Policy by default for most/all users in most cases. See itprotoday.com/management-mobility/… since I can't paste enough of it here to capture the list of what gets the permission in what circumstances. – Rook Commented Feb 20, 2018 at 1:13
- Bypass Traverse Checking as a right is also there as an NTFS performance enhancement to permit skipping checking the permissions of each folder in the tree on the way to opening the final desired folder/file, so it's not suggested to remove it unless you know you need that extremely high level of security. – Rook Commented Feb 20, 2018 at 1:15
One solution similar to MDMarra is set NTFS permissions as follows:
- dir1 : Grant List folder contents (Traverse folder/execute file, List folder/read data, Read attributes, Read extended attributes, Read permissions)
- BUT select This folder only for Apply to dropdown
- dir2 : Grant List folder contents and Apply to This folder only
- dir3 : Grant desired Read/Write permissions and Apply to This folder, subfolders and files or Subfolders and files only
The end result is the user/group can read each individual parent folder and drill down to the child folder without any other folders or files.
- That’s not similar to MDMarra’s answer, that is MDMarra’s answer, spelled out in greater detail. – Scott - Слава Україні Commented Nov 15, 2017 at 15:59
So I've been testing this in the following environment as I wanted get a final, tested answer, on the bare minimum required permissions for simply traversing folders via browsing (i.e. through the Windows File Explorer). Here are the results for those who want to lock things down tight.
I have not tested this in production yet to see if there are any odd side-effects from paring down the "standard" well-tested traversal rights template of
- Traverse Folder
- List Folder
- Read Attributes
- Read Ext. Attributes
- Read Permissions
...which is basically just normal "Read And Execute" permissions limited to "This Folder". That said, small-scale testing has been completely fine so far for users simply moving, copying, and removing files on the server and users completely working off of the server copies of documents, etc.
Environment:
- Server : Windows 2008 R2 -- Little to not Group Policy, nothing changed relating to user rights, configured as a domain controller, AD-integrated DNS, very standard/basic setup.
- Client : Windows 7 SP1 -- Clean install in a VM, restarted between any changes to ensure the connection to the server was fully recreated each time.
- Both installations patched to at least late 2017, so likely current for anything related to permissions which are very baked-in at this point in the Windows timeline.
- This was accessing a shared folder mounted as a persistent network drive (\server\share -> S:) in the VM. Share permissions were Read+Change for Authenticated Users group which covers the test user and all others likely to ever need access at some point.
- After each change I would restart the VM, open the File Explorer, and simply browse the share normally, going down a path I knew the test user had these traversal rights on vs ones it didn't.
- Required on Root Folder : ListFolder-ReadData + ReadAttributes (2x permissions)
- Required on Subfolders : ListFolder-ReadData (1x permission)
Optional : TraverseFolder--ExecuteFile
--> This optional permission only matters if Bypass Traverse Checking User right was explicitly disallowed, as it is on by default in 99% of circumstances. Put differently, the "Bypass Traverse Checking" user right (exposed in Group Policy, not in NTFS file/folder permissions) being enabled obviates this privilege completely and effectively makes this privilege enabled everywhere by default. Note: I have not tested to see if an explicit deny of this right would, in turn, stop the Bypass Traverse Checking user right from taking effect in that particular instance, but it might).
Supplementary Info: The "Bypass Traverse Checking" user right allows someone to passively traverse to a subfolder, however many levels deep, that they have access to directly (i.e. the permissions are set on that file/folder, but not necessarily anywhere else further up the file path).
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged ntfs windows-server-2003 symbolic-link junction ..
- The Overflow Blog
- Why do developers love clean code but hate writing documentation?
- This developer tool is 40 years old: can it be improved?
- Featured on Meta
- The December 2024 Community Asks Sprint has been moved to March 2025 (and...
- Stack Overflow Jobs is expanding to more countries
Hot Network Questions
- Does the wave function of a group of particles collapse upon a collective measurement?
- Makefile for a tiny C++ project
- Why don't the Bene Gesserit retaliate against Vladimir Harkonnen for trying to kill Jessica and Paul?
- I probably disallowed using the camera at some time in the past and now can't find a way to allow it again. How can I reenable it?
- Combining outer product of two lists
- Movie ends with wall mounted alien hand moving. Poison lump on hand
- QSpice sim results
- Writing rhythm/slash notation on a single line staff?
- More efficient way to color-code cycle permutation list
- Participle clauses - the appropriate form of some participles
- Reference request concerning Frege on truth?
- How to differentiate coyote vs wolf tracks
- What does this statement actually mean?
- Auto-configuring Global Unicast address with prefixed other than 64-bits len
- PSE Advent Calendar 2024 (Day 21): Wrap-Up
- What's the white substance spread across this thermal fuse and these two resistors?
- Are linear mixed effects model robust to unbalanced clusters?
- Do relativistic propagators give probability amplitudes?
- C++20 Robust File Interface
- Is 骰子 pronounced "shăi zi" or "tóu zi"?
- Why is it YHWH and not 'HYH?
- Left Justified Above Caption in hvfloats
- Systemd service to start only after CIFS mount
- How to read this old French speed gauge?

COMMENTS
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on. ... that are concerned about security may want to remove the Everyone group from the list of groups that have the Bypass traverse checking user right. Taking explicit control over traversal assignments can be an effective ...
A: If a Windows account is granted the Bypass Traverse Checking user right, the account—or the process that acts on behalf of the account—is allowed to bypass certain Windows security checks. Bypass Traverse Checking determines which users can traverse directory or file system folder trees even though they might not have permissions on the ...
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on. ... we recommend that you thoroughly test any changes to assignments of the Bypass traverse checking user right before you make such changes to production systems. In particular, IIS requires this user right to be assigned ...
WinSecWiki > Security Settings > Local Policies > User Rights > User Rights In-Depth > Bypass traverse checking. Bypass traverse checking AKA: SeChangeNotifyPrivilege, Bypass traverse checking. Default assignment on workstations and member servers: Administrators, Backup Operators, Power Users, Users, Everyone
Check User Rights How to get it. Get-UserRights.ps1 Direct Download Link or Personal File Server - Get-UserRights.ps1 Alternative Download Link or Personal File Server - Get-UserRights.txt Text Format Alternative Download Link. In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your PowerShell ISE and press play.
Inappropriate granting of user rights can provide system, administrative, and other high-level capabilities. Accounts with the "Bypass traverse checking" user right can pass through folders when browsing even if they do not have the "Traverse Folder" access permission. They could potentially view sensitive file and folder names.
Navigate to Local Computer Policy -> Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment. If any accounts or groups other than the following are granted the "Bypass traverse checking" user right, this is a finding: Administrators Authenticated Users Local Service Network Service
This user right determines which users can traverse directory trees even though the user may not have permissions on the traversed directory. This privilege does not allow the user to list the contents of a directory, only to traverse directories. This user right is defined in the Default Domain Controller Group Policy object (GPO) and in the local security policy of
"Windows 10 User Rights Assignment" and select Save. Lets Start with "Load and unload device drivers." Select Add on the next Page. Enter in the name for the setting. I am preceding the name with URA (for User Rights Assignment). ... BUILTIN\Administrators SeChangeNotifyPrivilege (Bypass traverse checking): BUILTIN\Backup Operators ...
Server: Windows 2008 R2 -- Little to not Group Policy, nothing changed relating to user rights, configured as a domain controller, AD-integrated DNS, very standard/basic setup. Client: ... The "Bypass Traverse Checking" user right allows someone to passively traverse to a subfolder, however many levels deep, that they have access to directly (i ...